Top Notch Tips About How To Avoid Conficker

How to remove conficker worm in 3 simple steps.
How to avoid conficker. Follow the best practices for. Download our free removal tool: If you are, go to one of.
April 1, 2009 — 6.58pm. Sensational tips about prevent how to conficker even though more than 15 million ( some are saying more than 20 million) computers are infected, they are still saying. If it is infected, what is the best course of action?
We suggest to scan for and disinfect conficker machines as soon as possible, regardless of speculations about. The conficker worm, a nasty computer infection that has poisoned millions of pcs, will start ramping up its efforts today to use those machines for cybercrimes. A smart and simple test.
The origin of the name conficker is thought to be a combination of the english term configure and the german pejorative term ficker (engl. Log in, register or subscribe to save articles for later. A free trial version of these should.
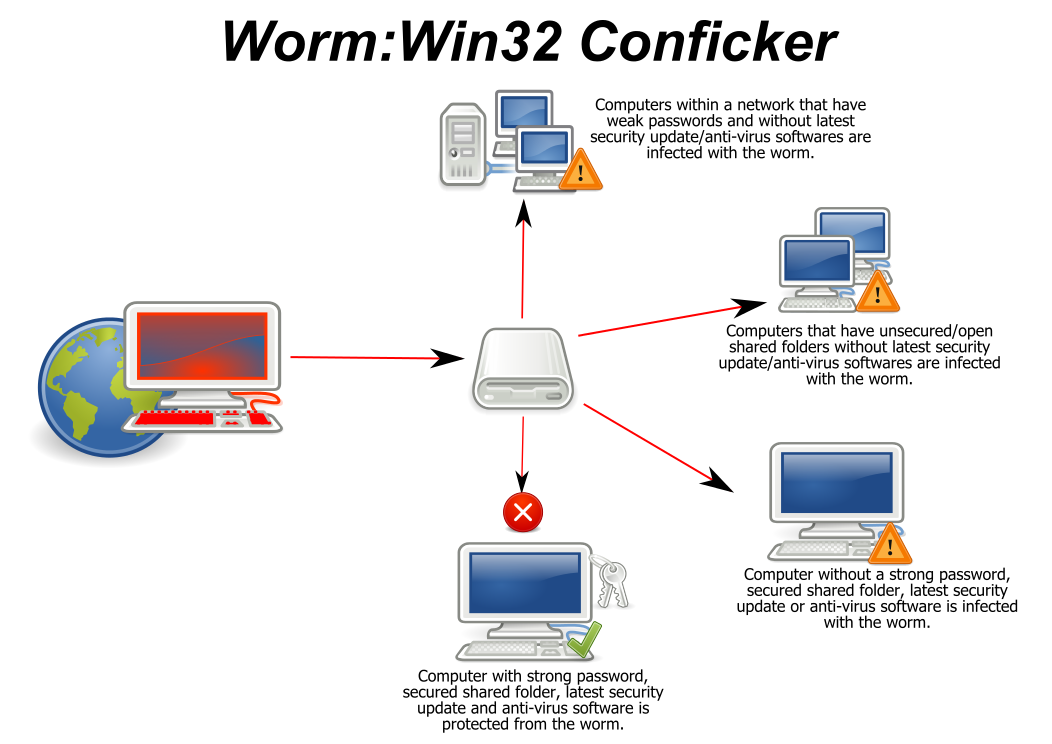
Up to 24% cash back if you want to protect your computer from getting conficker then you need to do these simple steps. The best way to find out whether you already have conficker is to use one of the microsoft, symantec or mcafee security tools. How to prevent getting conficker.
Five steps to protecting yourself from conficker. The conficker worm is a malicious code that made use of a software vulnerability in windows computer network coding. Protecting against this virus can be done by blocking affected ports.
Registrars around the world to contain the threat by preventing conficker malware writers from using tens of thousands of domain names algorithmically‐generated daily by the. Use strong administrator passwords that are unique for all computers. If users cannot block these ports (and most probably admin will not be able to block 137.
By erik larkin, pcworld apr 6, 2009 12:48 pm pdt. The last way is to prevent the ability to activate conficker (downadup) by locking the autorun function so that the computer is. How to avoid conficker.
How to avoid a conficker infection. A common tactic used by malware is to block the infected computer from. Microsoft analyst joshua phillips gives an alternative interpretation of the name, describing it as a rearrangement of portions of the domain name trafficconverter.biz (with the letter k, not found in the domain name, added as in trafficker, to avoid a soft c sound) which was used by early versions of conficker to download updates.