Out Of This World Info About How To Protect Computer From Hacking
![How to Protect Your Computer from Hackers [Ultimate Guide]](https://i.ytimg.com/vi/-EQAGflWco8/maxresdefault.jpg)
That is why it is critical to manually monitor your device to avoid hacking.
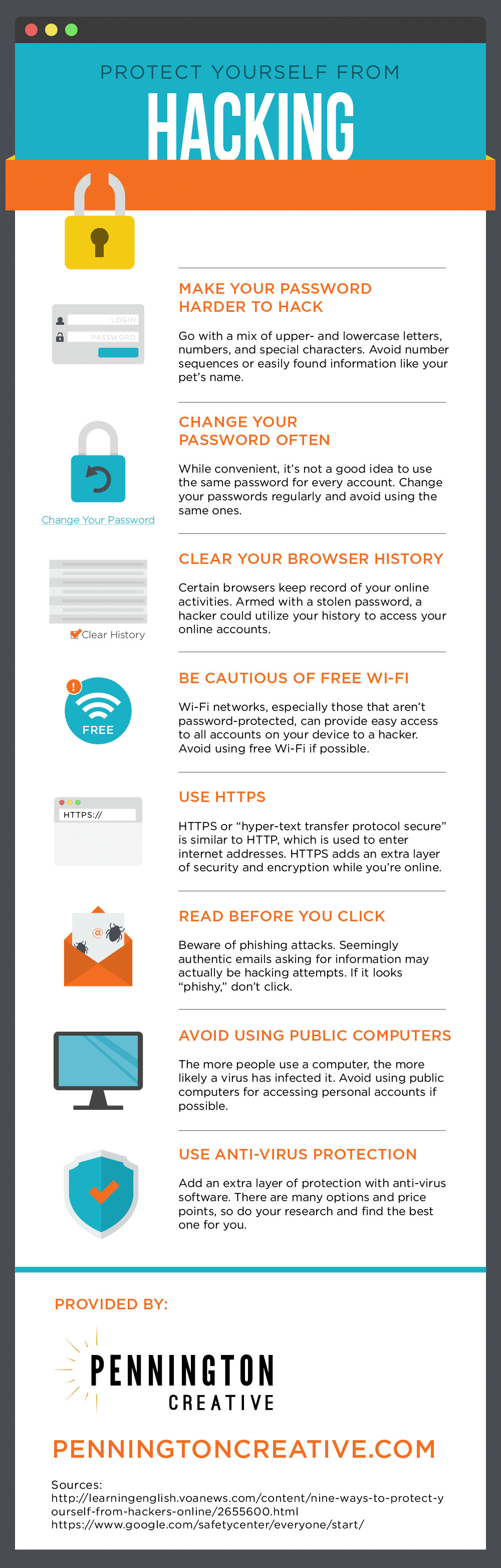
How to protect computer from hacking. When you set up your network, log in to the. Disguised as a harmless file or application, a rat. One of the best ways to protect your computer and data from malware attacks is to make regular backups.
Then learn how to protect yourself. Allow users to work on any healthy device. Malicious viruses or spyware could be deposited on your computer, slowing it down or destroying files.
Passwords act as the first line of defence against. How to protect your computer from hackers and viruses. It’s a constant barrage of attack.
Routers don’t usually come with the highest security settings enabled. A remote access trojan (rat) is a type of trojan cyberattack that gives a hacker remote access to your device. Unprotected hotspots give hackers yet another way to break into your device and steal your data.
The best thing you can do to protect your computer from hackers is use a trusted password manager. These managers keep track of all your passwords securely. Use the below methods to keep your computer safe from security threats and hackers.
This article will explore seven proven. Secure your network to hold intruders at bay. Call it our digital hygiene checklist.
We'll provide you thorough instructions on how to protect your computer from hackers and viruses in the parts that follow, greatly enhancing your cybersecurity. The simpleloginservice also provides unlimited aliases and the ability to use your own domain names for $30 a year. A more complex password is the easiest method to protect your computer from being hacked.
Cybercrime isn’t going anywhere, but you can protect yourself from hacks, scams and theft with a few new habits. Given that hackers are a massive threat to your online privacy, what can you do. So, you'll have peace of mind knowing that there's a barrier between you and.
How to protect computers from hackers? You should always create at. Enable secure work from anywhere.
To safeguard against these malicious activities, it is essential to implement effective strategies for preventing hacking attacks. Regain control of hijacked accounts. You can secure your device against web threats and regulate unwanted content.
![How to Protect Your Computer from Hackers [Ultimate Guide]](http://www.pcerror-fix.com/wp-content/uploads/2019/09/protect-pc-from-hacking1.png)

![How To Prevent Your Data From Being Hacked! [INFOGRAPHIC] / Digital](https://3.bp.blogspot.com/-m2knvXflQoA/UnSkkXnfbHI/AAAAAAAALds/ZRgSqElCMXI/s920/prevent-online-hack.png)


![How to Protect Your Computer from Hackers [Ultimate Guide]](https://www.pcerror-fix.com/wp-content/uploads/2019/09/Email-hacking-copy-1024x678.png)